Home > Products > SIEM & XDR
SIEM & XDR

SIEM - Log management, and Threat detection.
SIEM software solutions and log management tools, which serve a specific purpose, offer significant value in terms of security information. However, their implementation often necessitates costly and time-intensive integration endeavours to consolidate log files from various sources, including asset inventory, vulnerability assessment, endpoint agents, and IDS products. Once in possession of the acquired data, it becomes imperative to diligently conduct thorough research and subsequently formulate correlation rules that will effectively discern potential threats within your operational environment. The complexity of these challenges increases exponentially when transitioning workloads and services from on-premises infrastructure to public cloud environments.
In the current landscape of IT teams facing limited resources, the allocation of time and financial resources towards the implementation of a Security Information and Event Management (SIEM) solution significantly hampers their ability to promptly identify potential threats. Consequently, this delay adversely impacts the overall return on investment.
Consider the inherent benefits of employing all-in-one security essentials in contrast to conventional Security Information and Event Management (SIEM) solutions:
• Discover a smarter way to prioritize your incident response
• Investigate threats deeper with advanced security analytics
• Stay vigilant with threat intelligence updates from VNK CSI’s Agency Defense Labs

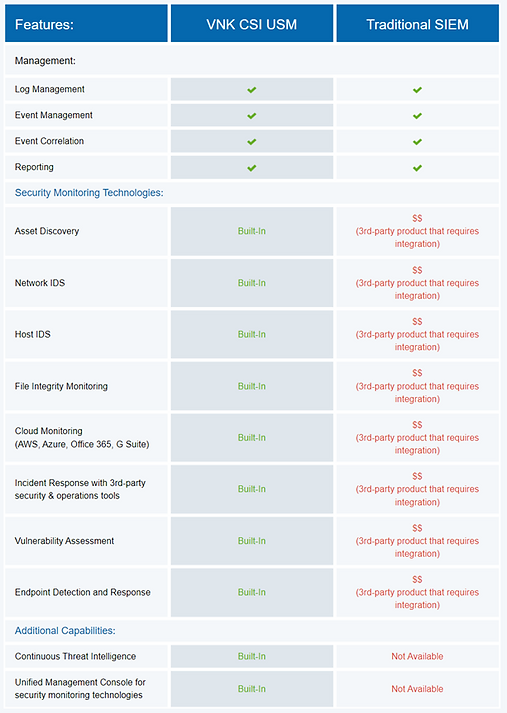
See how all-in-one security fundamentals beat SIEM.
Traditional SIEM software promises everything you need, but the way to get there is too expensive for most of us. Traditional SIEM systems analyse security tool and log data, which may be costly and difficult to implement and integrate. They need regular fine-tuning and rule drafting.
USM offers an alternative. USM integrates the critical security features required for full and effective threat detection, incident response, and compliance management—all on a single platform with no extra feature costs. The USM platform is ideal for organisations of all sizes due to its simplicity and quick ROI.
Prioritise incident response intelligently.
USM alarms provide threat information, including attack techniques, associated events, source and destination IP addresses, and incident response remediation advice, so you can analyse and react to attacks quickly. USM reduces false positives and loud alerts to improve productivity.
The kill chain taxonomy employed by USM effectively categorises attacks into five distinct threat categories. This approach facilitates the seamless identification of attack intent and the evaluation of threat severity by analysing the way threats interact with your environment.
System compromise
Behavior indicating a compromised system.
Exploitation & installation
Behavior indicating a successful exploit of a vulnerability or backdoor/RAT being installed on a system.
Delivery & attack
Behavior indicating an attempted delivery of an exploit.
Reconnaissance & probing
Behavior indicating a bad actor attempting to discover information about your network.
Environmental awareness
Behavior indicating policy violations, vulnerable software, or suspicious communications.
Enhance threat intelligence by leveraging cutting-edge security analytics to conduct in-depth investigations.
Perform a comprehensive search and meticulous analysis of the pertinent events.
Within the USM (Unified Security Management) system, users are empowered with seamless access to pertinent security data, ensuring optimal efficiency in incident investigation. This is facilitated through the utilisation of intuitive search and filter functionalities, enabling swift and effective analysis. Within the USM platform, it is conveniently feasible to:
• Search events to identify activity and trends
• Apply filters to find more granular data
• Sort by event name, IP address, and more
• Create, save, and export custom data views
• Generate custom reports from any view or leverage pre-built templates
• Examine raw log data related to alarm activity
• Access OTX pulses and “happening now” security information
Asset, event, and vulnerability security visibility
• View asset alarms and events.
• Actively request endpoint information
Know whether your vulnerabilities impact high-priority or business-critical assets.
• Link vulnerabilities to attacks
• View the events that caused an alert by drilling down.
• View forensics data on event triggers
• Launch pre-built forensics and response actions immediately from an event or alert.
• Use a completed action to create an orchestration rule for future alarms and events.

Extended Response (XDR) - Our complete solution gathers telemetry and other data from your attack surface and applies security analytics and machine learning to improve incident response.
Protect, identify, and react to new threats at scale.
Automatic danger detection and response
Automate security analytics and incident response.
Single-pane glass
To swiftly and effectively react to attacks, centralise visibility of all attack surface tools and assets.
Don't tear and replace.
An open platform that keeps your security products.
High-touch managed service
Our technology, infrastructure, and knowledge can secure your organisation.
Increase detection and responsiveness.
Prevent endpoint malware and ransomware.
Machine-learning endpoint security detects threats by behaviour rather than signature.
Find and stop network attackers
Our award-winning USM platform automatically gathers and analyses data across your attack surface to provide context for quicker, more accurate threat detection and coordinated, efficient incident response.
Security overview
Get a centralised view of your network, endpoint, cloud, and SaaS assets and vulnerabilities.
High-touch service for your security team
Access a managed security operations centre (SOC) with broad data gathering, automated threat detection and response, Agency Defence Labs threat intelligence, and several third-party app connectors



